Civilian
Protecting Government Systems and Data
Enhancing overall cybersecurity and resilience is critical to protecting the mission of every federal agency. Seeing, protecting and managing your entire attack surface is key. Yet many Federal agencies experience a “visibility gap” where IT and security leaders are blind to the vulnerable and at risk assets within their environment. And with the growing complexity of digital environments, strict regulation and compliance requirements, continued migration to the cloud, convergence of IT/OT/IoT–coupled with limited funding and internal resources–achieving comprehensive security is a persistent challenge. Agencies need a new, modern approach to cyber exposure management and security.
Complete Asset Visibility
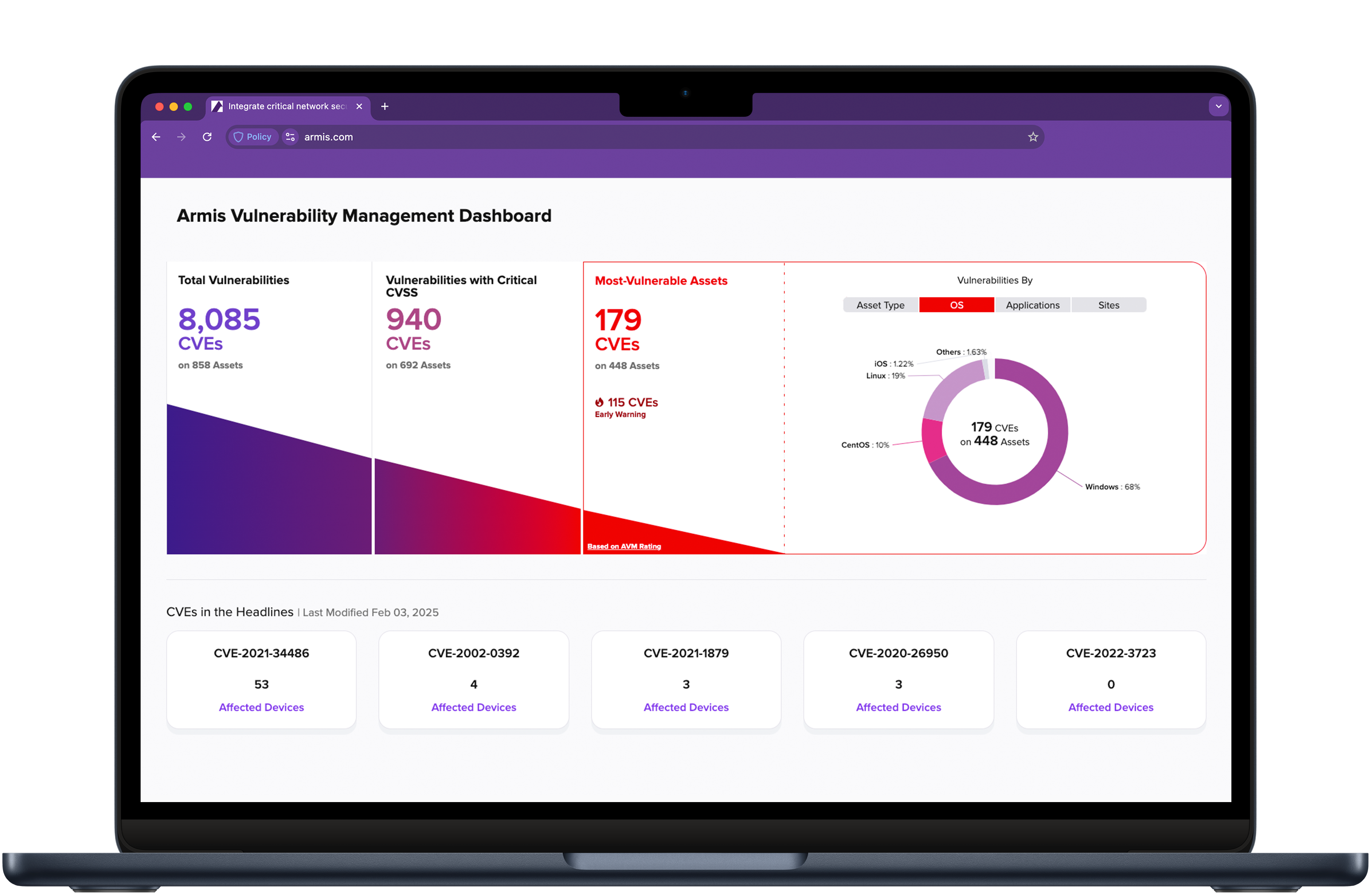
According to Armis Labs, 40% of assets that are connected to the network are unmonitored. Agency IT leaders must gain complete visibility into the assets in their environment and deep situational awareness to know precisely which assets may become vulnerable and pose a threat. Armis Centrix™ helps government agencies remove the visibility gap and provides a holistic picture of your risk posture with oversight into all connected assets in your environment in real time.
Addressing the Unique Challenges of Civilian Agencies
The need to modernize CDM
Despite the tremendous efforts of the Continuous Diagnostics Mitigation (CDM) program over the last decade, agencies still lack complete contextual visibility. Striving to reduce the threat surface, increase visibility into their cybersecurity posture, improve cybersecurity response, and streamline FISMA reporting, federal agencies are experiencing visibility gaps and problems of perspective due to an explosion of endpoints.
Shadow IT and bottom-up budgets mean IT and security leaders do not manage nor are even aware of all the vulnerable assets in their environment. It’s time for the CDM program to actively empower your agency, rather than place undue burdens.
The need for a zero trust architecture
If there is one thing the entire federal government can agree on, it’s that Zero Trust is the best approach for stronger cybersecurity. It is critically important that ALL assets and systems are accounted for in a Zero Trust approach.
The need to include every asset in a Zero Trust approach is made clear in NIST Special Publication 800-207, a foundational document meant to provide an implementation roadmap for Zero Trust security concepts.
The need for state-of-the-art infrastructure
Many federal agencies still rely on legacy systems and outdated IT infrastructure that may be vulnerable to cyberattacks. Transitioning to more secure and up-to-date cyber exposure management and security technology is essential to reduce risk and enhance cybersecurity.
Programs like CDM aim to tackle this challenge as legacy solutions cannot address the inherent risks posed by a lack of visibility and contextual intelligence of all assets. The bold changes the government has called for require a collaborative and inclusive procurement directive free from legacy models, contracts, or solutions. What worked in years past is no longer fit for purpose.
Enabling the Mission with Armis Centrix™
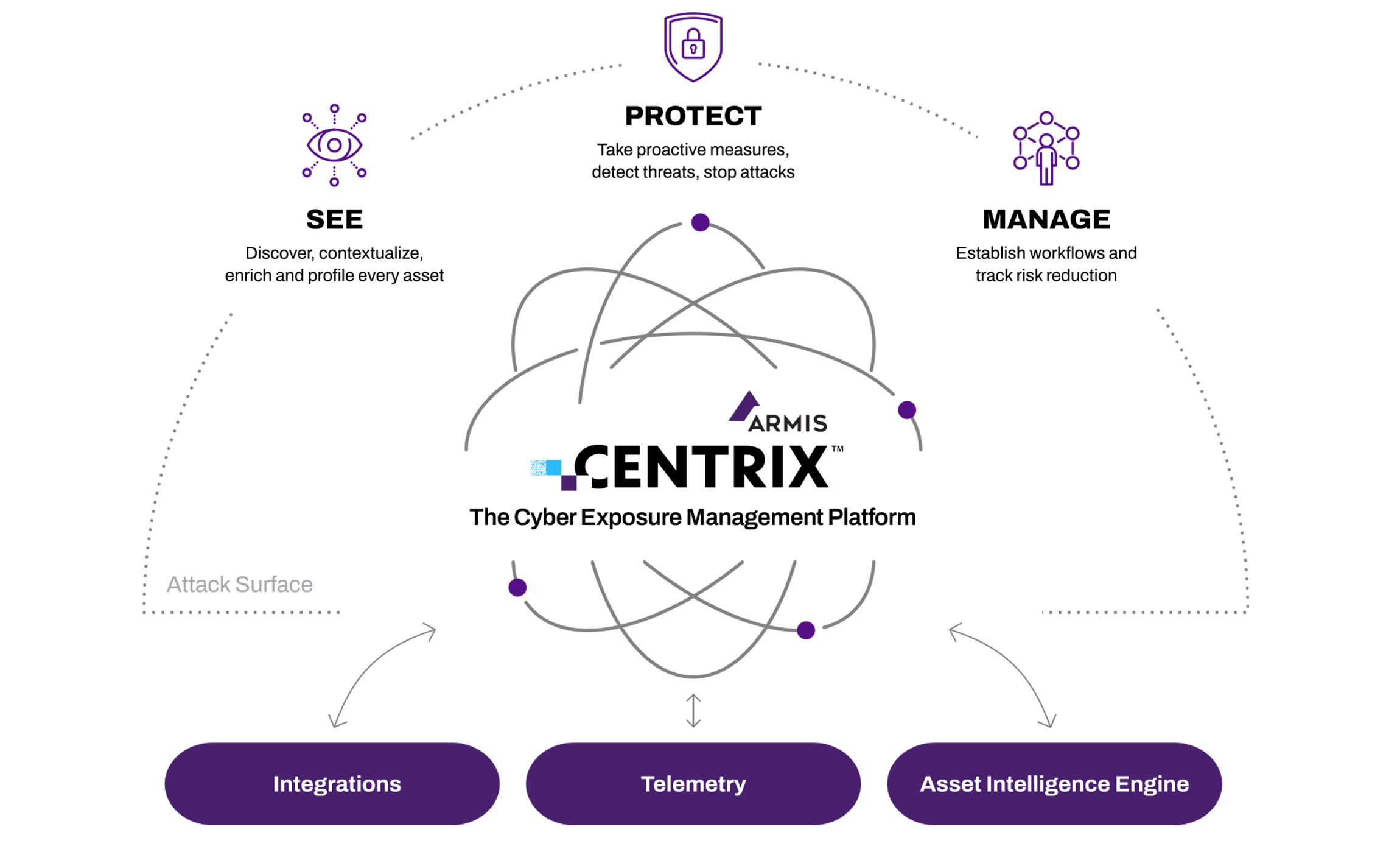

Immediate Time-to-Value
Fast and easy, and requires no additional hardware.
Asset Management and Security
Discover and classify every device in any environment.

Asset Intelligence
Gain the intelligence required from the Armis Asset Intelligence Engine which monitors and profiles billions of assets world-wide to identify cyber risk patterns.
Dynamic Risk Assessment
Individual risk assessments for each device based on real time intelligence and dynamic operating environments.
Vulnerability Management
Identify risk, deduplicate, contextualize, prioritize and assign in order to take the right action at the right time.
Meaningful Integrations
Through collaboration and information exchange, extract more value from investments in existing IT and security tools.